King of the Hill: A Novel Cybersecurity Competition for Teaching Penetration Testing
ABOUT
King of the Hill (KotH), an active learning cybersecurity competition
designed to give students experience performing and defending against
penetration testing. KotH participants must consider real-world
trade-offs that professional pentesters face, like what services to run
or restrict, what machines in the network can be used to gain access to
others, and more.
King of the Hill also opens up a number of new teaching opportunities for educators. We have run KotH competitions in our classes; if you are interested in having an engaging, exciting in-class pentesting competition, read more below. Our code and network design are publicly available.
King of the Hill also opens up a number of new teaching opportunities for educators. We have run KotH competitions in our classes; if you are interested in having an engaging, exciting in-class pentesting competition, read more below. Our code and network design are publicly available.
WHY DO WE NEED ANOTHER CYBERSECURITY COMPETITION?
Cybersecurity competitions are an effective and engaging way to provide
students with hands-on experience with real-world security practices.
Capture-the-flag competitions (CTFs) gives participants experience with
offensive technologies; Build-it/Break-it/Fix-it gives experience in
writing and attacking secure software.
Unfortunately, existing competitions are ill-suited in giving students experience in penetration testing, because they tend to lack three key aspects:
Unfortunately, existing competitions are ill-suited in giving students experience in penetration testing, because they tend to lack three key aspects:
- Pivoting: In real-world networks, rarely are all machines (and all vulnerabilities) directly accessible from all other machines. Real pentesters must pivot from one compromised machine to another in order to gain access to more machines. KotH competitions take place over nontrivial network topologies; some machines can be reached only by taking control of machines along the way.
- Implants: After gaining access to a machine, pentesters often have the opportunity to leave behind implants: their own software that, for instance, opens a backdoor, closes vulnerabilities from other attackers, and so on. KotH participants are encouraged (and, in our class, required) to write implants that patch existing vulnerabilities and introduce backdoors so that they can retake machines they lose control of.
- Preparation: Professional pentesters often have time to prepare by performing reconnaissance, scanning a network, and writing their implant code. KotH addresses this by giving participants weeks ahead of the competition to prepare their patches and implants.
HOW DOES KotH WORK?
KotH participants are divided into teams, and each team must work
together to attack, control, and defend as many computers on a target
network as they can.
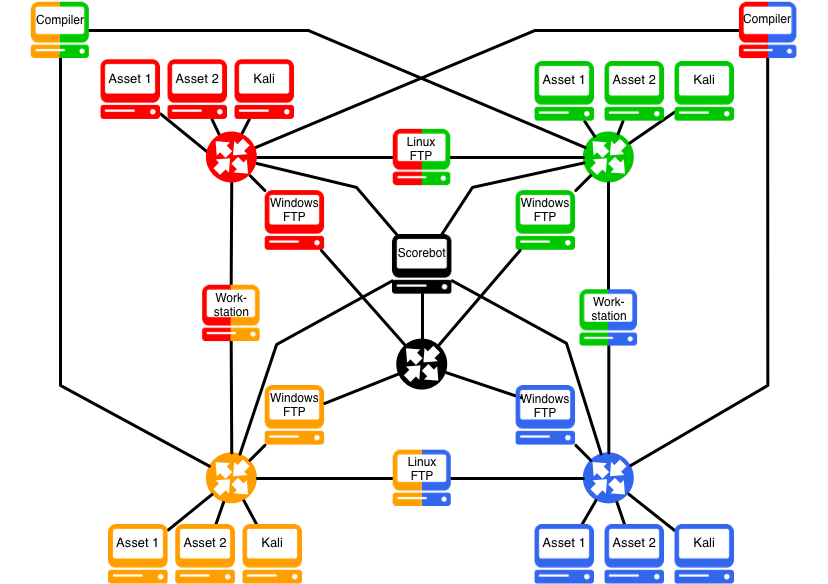
Gameplay occurs over a large, complex, isolated virtual environment, comprised of vulnerable Linux and Windows virtual machines of various builds that are spread across multiple partially interconnected subnet- works. Below is an example network we used in a recent competition:
Here, there are four teams — Blue, Green, Orange, and Red — each of these teams must pivot repeatedly in order to reach many of the machines in the virtual environment.
Each team's goal is to exploit as many vulnerable machines on the network as they can, claim them by calling out to the global scorebot, defend them from other teams, and protect their critical services.
Teams earn points keeping critical services up-and-running on the machines they control. They therefore have to consider the real-world trade-offs between keeping a vulnerable service up or shutting it down to help keep the rest of their network safe from attack.
For detailed information, please view our ASE 2018 paper.
Gameplay occurs over a large, complex, isolated virtual environment, comprised of vulnerable Linux and Windows virtual machines of various builds that are spread across multiple partially interconnected subnet- works. Below is an example network we used in a recent competition:
Here, there are four teams — Blue, Green, Orange, and Red — each of these teams must pivot repeatedly in order to reach many of the machines in the virtual environment.
Each team's goal is to exploit as many vulnerable machines on the network as they can, claim them by calling out to the global scorebot, defend them from other teams, and protect their critical services.
Teams earn points keeping critical services up-and-running on the machines they control. They therefore have to consider the real-world trade-offs between keeping a vulnerable service up or shutting it down to help keep the rest of their network safe from attack.
For detailed information, please view our ASE 2018 paper.
CODE AND DATA
All code and data are available on the KotH GitHub repository.
PUBLICATIONS
PEOPLE
The following people have contributed to this project:
- Kevin Bock (University of Maryland)
- George Hughey (University of Maryland)
- Dave Levin (University of Maryland)